Set Up Office 365 Authentication
To authenticate against Office 365, perform the steps in this article.
1 Add the security provider dependency
To add Office 365 as a security provider in the Oauth Security module:
-
Remove any existing security provider dependency from the
pom.xmlunder the root of the project. -
Add a security provider dependency for Office 365 to the
dependenciestag inpom.xml:<dependency> <groupId>twigkit</groupId> <artifactId>twigkit.security.provider.oauth.office365</artifactId> <version>${project.parent.version}</version> </dependency> -
Configure Appkit to invoke the Oauth Security module on startup. Change the
security.conffile insrc/main/resources/conf/security/to contain:type: oauth
You must remove any existing spring-security.xmlfile because this module encapsulates all Spring configuration automatically.
2 Configure the OAuth module for the application setup in Azure AD
Add the relevant configuration in a file in conf/security/oauth.conf:
azure-ad-tenant-id: 746a834e-ba89-4191-926d-f2c220b79a4a
resource: https://your-organisation.sharepoint.com/
client-id: 08de5b32-569a-4387-ab94-08b7b6fc1ed8
client-secret: x7vRc8VJ9CHjSM5XXyHpCSRaD5JH/6VsB8P5ZGz4B8M=This guide assumes these settings have already been set up in the Azure AD instance in Microsoft’s Azure portal and provided to you as an application developer.
The reply URL must be configured in Azure AD as http://your-application-url/oauthLogin.
|
3 Add the Spring filter to the web.xml file
Add this to the web.xml file of the project:
<!-- Spring Security -->
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>classpath:spring-security.xml</param-value>
</context-param>
<listener>
<listener-class>org.springframework.web.context.ContextLoaderListener</listener-class>
</listener>
<filter>
<filter-name>springSecurityFilterChain</filter-name>
<filter-class>org.springframework.web.filter.DelegatingFilterProxy</filter-class>
</filter>
<filter-mapping>
<filter-name>springSecurityFilterChain</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
<listener>
<listener-class>
org.springframework.web.context.request.RequestContextListener
</listener-class>
</listener>
<!-- Spring Security Ends -->Inclusion of a 'RequestContextListener' is not required in a standard Appkit-plus-Spring Security application.
4 Test the authentication
If a user is not logged into Office 365 prior to visiting the application, then they will be redirected to the Microsoft Online login page.
If the Azure administrator has set app approval explicitly, after the user is logged in, the user will be returned to the application as an authenticated user.
The Appkit user’s details will be populated with any basic information available from the decoded OAuth token such as first name, last name and email address.
If approval is not set by the Azure AD administrator, then there will be an intermediary step after the user logs into Microsoft Online requesting their explicit approval for the application to access their credentials.
Using OAuth can create a seamless experience where, after the token handshake and approval is complete, the user will always be logged into the application as long as their session with Microsoft Online/Office 365 is active.
User logs in:

User approves application:
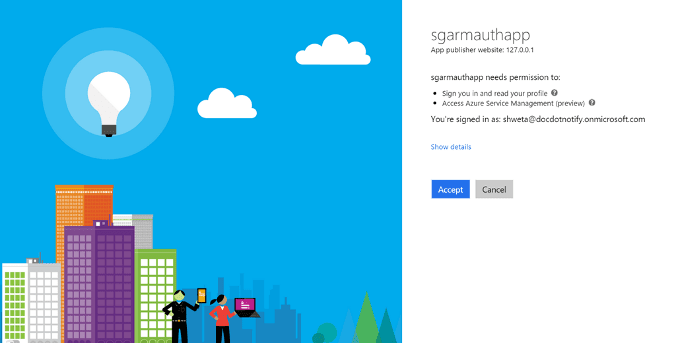 (This is optional, depending on the Azure AD configuration.)
(This is optional, depending on the Azure AD configuration.)
The user is signed into the application with an OAuth token, and will be signed in automatically from now on unless the token expires or the user logs out of Office 365 entirely.